With the increasing rate of daily cyber-attacks, it is clear that no one is safe from data breaches or cyber-extortion. In most cases, access to an individual or organization’s systems is often gained by fooling people within to do things they shouldn’t, such as clicking on a link or opening a document.
Spear Phishing and Whaling aim to deceive individuals to gain access to sensitive information. Though their methods and targets differ significantly, spear phishing and whaling can negatively affect businesses.
Are you wondering what the similarities and differences between spear phishing vs whaling are? Keep reading to understand these cyber-attacks and learn how to protect yourself from these malicious acts.

What is Phishing
According to research by Verizon, about 30% of data breaches stem from phishing attacks. Phishing is a cyber-attack where an attacker sends emails or messages to individuals within an organization, pretending to be a known or trusted source. The goal is to deceive the recipients into revealing sensitive personal information.
Phishing attackers prioritize quantity over quality, sending the same generic message or email to multiple organizations to maximize the number of potential victims. However, a poorly crafted phishing message often contains many errors and inconsistencies, making it easily detectable.
Common Features of Phishing Emails
Phishing emails can appear legitimate communications from trusted sources since they often seem real. However, a closer inspection can show signs that can help identify these fraudulent messages, such as:
- Grammatical Error – One of the common indicators of phishing is grammar and spelling errors. Cybercriminals often rush to send out as many emails as possible, neglecting to proofread their messages, so grammatical errors usually serve as an immediate red flag.
- Juicy Offers – Some phishing emails frequently lure recipients with offers that seem too good to be true, such as winning an iPhone, getting lots of cash, etc. This is usually sent with promises that require no hard work but only malicious mail.
- Generic Greetings – Phishing mail is usually not personalized, as it is mostly sent to a group of people. It is important to look for greetings such as “Dear Customer” and other related generic greetings.
- Urgent Action Demands – Creating a sense of urgency can cloud judgment and lead to hasty actions without proper verification. The mail usually contains content that requires fast action due to the limited time. Sometimes, it could have messages like “your account will be suspended” if no action is taken quickly.
- Inconsistent Email Addresses – Pay attention to the email addresses, links, and domain names, as they will try to mimic the actual source. There will always be an error in the email address since it is from a different source.
What is Spear Phishing?
Unlike general phishing attacks that are sent together to numerous recipients, spear phishing emails are customized to the targeted victim, making them more convincing and harder to detect.
Spear phishing is a type of phishing where the attacker sends emails, text messages, or instant messages as though they are from a known or trusted source in order to prompt targeted individuals in reputable organizations to reveal sensitive data or information.
This attack is usually targeted at employees of organizations who are tricked into sending sensitive information, downloading and installing malicious software, or sending unauthorized payments to the perpetrator.

Spear phishing is always well-planned and not random. The attacker is always someone who has studied the organization properly. They do this by inserting spyware in the company’s system to monitor and capture private information on how the company operates and the patterns of mail usually received by staff.
Cybercriminals use this information to plan a more realistic attack on the employees, making it difficult for the victims to detect and shield themselves from the attack.
Examples of Spear Phishing Attacks
Spear phishing attacks are sophisticated and highly targeted, making them more challenging to detect compared to generic phishing attempts. Understanding specific examples of spear phishing, you can better recognize and mitigate these attacks. Below are 4 main examples of spear phishing, showcasing different tactics used to deceive and manipulate targets.
- Bank transfer fraud – Bank transfer fraud involves attackers impersonating trusted entities to deceive individuals into transferring funds to fraudulent accounts. This attack is highly targeted and leverages social engineering tactics to exploit the trust and authority relationships within an organization or individual.
- Lottery scams are a form of spear phishing where attackers deceive individuals into believing they have won a lottery or sweepstakes prize. The goal is to extract personal information, steal credit or debit card details, or install malware on the victim’s device. These scams are often targeted using information about the victim to make the scam appear more credible.
- Employee fraud – Employee fraud is usually known as “internal fraud”. This is because it is carried out by an employee of the company in situations where the company has a weak security system or poor staff management.
- Payroll fraud is a targeted cyberattack where attackers manipulate payroll processes to divert payments or steal sensitive employee information. For example, an attacker can target the HR department, requesting sensitive payroll information by impersonating the company’s CFO.
What is Whaling
A whaling attack is a type of phishing focused on a company’s senior players, such as CEO, CFO, Finance manager, etc. The aim of this attack is to majorly get money as well as sensitive information regarding the company.
According to GreatHorn, incidences of whaling and executive impersonations increased significantly by 131% after the shift to remote working in 2020. Unlike spear phishing which targets particular individuals who are mid or junior staff, whaling targets the top-level staff in the company. You can see them as “Whales” of the company, hence the name ” Whaling”.
Information used for this attack can be obtained from the individual’s system, social media account, etc. The imposter might come as a business partner or a business friend requesting for money as a known person.
Examples of Whaling
Whaling attacks aim to exploit the authority and access privileges of high-ranking individuals to steal sensitive information, commit fraud, or gain unauthorized access to the organization’s resources. See some examples of whaling attacks below:
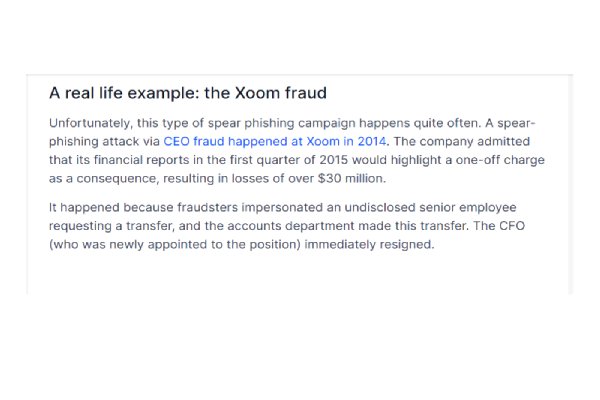
- CEO fraud – This involves the impersonation of an organization’s CEO in an email targeted at the employees. This might be a request to make a cash transfer or send in important documents. Employees ready to make a good impression will fall victim to such a scam. This fraud usually targets senior staff members who can approve payments or share vital information. See the image below for a real-life example of the Xoom fraud.
- Fake Legal Notice – A fake legal notice is a type of attack scam where attackers impersonate legal entities or authorities to create a sense of urgency and fear; prompting targeted individuals to take immediate action without thorough verification.
What is the difference between Spear Phishing and Whaling?
| S/N |
Differences |
Spear Phishing |
Whaling |
| 1 |
Target |
Individuals with access to company funds. |
C-level executives such as the CEO, CFO, CMO, or CTO. |
| 2 |
Design |
The emails or messages are prepared and sent to a group of employees in an organization |
The email is sent to a specific person, so it is well written. |
| 3 |
Value |
The target gives a good response and high-yield because the messages are personalized. |
Yields very fast high-value results due to the rank of people involved and the message sent. |
| 4 |
Example |
An email indicating that a specific payment could not be processed due to missing information, with malicious links provided to attempt the payment again. |
A professional email appearing to be from the CEO requesting to share private information such as employee payroll details. |
The main difference between spear phishing and whaling lies in the level of targeting and the potential impact of a successful attack. While spear phishing can compromise individual accounts and information, whaling has the potential to cause more extensive damage due to the high-level roles of the targeted individuals.
Similarities between Spear Phishing and Whaling
While whaling attacks are more valuable and damaging than spear phishing, understanding the similarities between spear phishing and whaling is important for implementing effective cybersecurity measures.
- Human Psychology Exploitation – Both spear phishing and whaling exploit human psychology as they create urgency or give the feeling of personalization. This makes it easy for the victim to take action quickly and without doubt of genuineness.
- Targeted Victims – Cyber-criminals pick their victims from a particular company or the same designation. The emails are not random, therefore making them difficult to detect.
- Channel of Attack – Attackers mostly use email, which is a company’s official communication channel. These emails are made to look almost authentic, thereby clearing all forms of suspicion.
How to prevent Spear Phishing and Whaling attack
Preventing spear phishing and whaling attacks requires an approach combining technological solutions, employee education, and robust security policies to mitigate the risks associated with these advanced forms of phishing. Below are great ways to prevent spear phishing and whaling attacks.
- Provision of security awareness training – Provision of security awareness training: If you’re a business owner, you need to include security training for all employees. This will help to fully equip everyone with the proper knowledge and reduce spear phishing risks.
- Strong Password Policies – Enforce strong password policies that require complex, unique passwords for all accounts. Also regularly prompting users to change their passwords and avoid using the same password across multiple accounts, reducing the risk of credential reuse in the event of a phishing attack.
- Implement Email Filtering Security Measures – Use advanced email filtering solutions to detect and block phishing attempts. These filters can identify suspicious links, attachments, and email addresses that may indicate phishing. Also, including an extra layer of security, such as MFA (Multi-Factor Authentication), is a good measure for accessing sensitive systems or performing important actions.
- Software and Hardware Updates – Keep your organization’s software and hardware updated to prevent unauthorized access. You can use comprehensive endpoint protection solutions that include antivirus, anti-malware, and intrusion detection systems (IDS) to detect and block phishing attempts at the endpoint level.
- Access Controls and Privilege Management – Implement strict access controls to ensure that employees only have access to the information and systems necessary for their roles. Using the principle of least privilege (PoLP) to regularly review and adjust access permissions can minimize the potential impact of a compromised account.
Conclusion
Cyber-attacks, including spear phishing and whaling are becoming advanced by the day. As attackers continually refine their strategies, we need to stay cautious and adaptive, regularly updating our defenses by creating a culture of security consciousness.